Ahoy wise captain! As ye sail the cyber seas, beware of hazardous waters teaming with ruthless buccaneers thirsty for plunder, sharks, and shoals. But with proper cybersecurity preparations and a trusty map, ye can traverse safely.
This cybersecurity guide maps some of the most common threats endangering voyages today and prudent protections to repel those digital pirates. Study the terms and processes carefully to prepare your crew.
Don’t Walk the Plank: Avoid These Devious Threats Lurking Below the Surface
You may find disaster and trecherrrry if you don’t heed these signs:
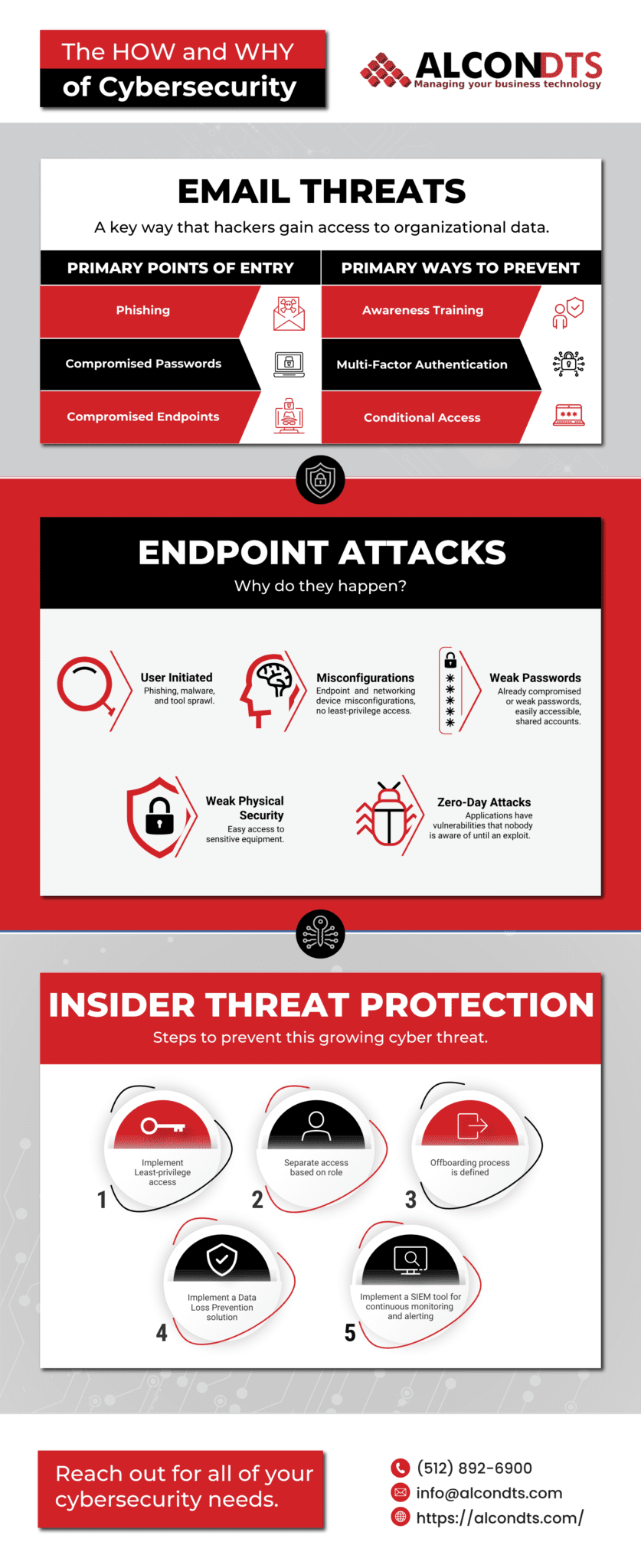
Insider Threats – Betrayals From Within
In addition to foreign foes, inside jobs jeopardize voyages. Corporate spy infiltration is rare but does make headlines. More often, carelessness causes calamity. Unchanged or simple passwords, unauthorized access, unlocked quarters – such mistakes create vulnerabilities. Limit damage and deter betrayal by instituting strict standards and access controls.
Phishing – Manipulation and Trickery
Phishing employs psychological tricks and technology to lure victims into crafty traps. Emails impersonating trusted parties convey fabricated emergencies demanding immediate login. Urgency pressures users to override caution. Clicking prompts credential theft. Spear-phishing focuses schemes on specific individuals, while whaling targets those highest in the ranks. Training all crew to identify subtle deceits helps avoid taking bait.
Ransomware – Vile Extortion
Ransomware bars access to systems until tribute is paid, with no guarantee of restored access. Designers carefully explore targets before encrypting and extorting high-value data and devices. Even if ransom is paid, they may sell your maps and treasure to the highest bidders.
Malware – Cursed Code
Malware secretly infects systems to steal data and control. Advanced strains scan logs, siphon records, and more. Polymorphic malware alters itself to avoid detection. Fileless versions leave no traces. Cryptocurrency schemes hijack systems for illicit coin mining.
Vulnerabilities – Unpatched Decks Left to Rot
Aging and neglected software/hardware become invisible vulnerabilities. Unpatched decks allow easy infiltration. Once defects become public knowledge upon repair, expedient upgrades are critical. Delaying maintenance heightens susceptibility considerably.
Man-in-the-Middle Attacks
Man-in-the-Middle attacks covertly intercept communication between two parties to steal data. The rogue eavesdrops on conversations, relaying messages without parties realizing. Unencrypted wi-fi and other weak points are often exploited.
Password Attacks
Password attacks seek to steal user credentials through phishing, brute force attacks, password spraying and more. Multifactor authentication thwarts many by requiring additional factors beyond a password.
SQL Injection Attacks
SQL injection inserts malicious code into database queries, tricking servers into revealing more data than intended. Input validation and prepared statements help stop SQL injection.
Zero-Day Exploits
Zero-day exploits take advantage of undisclosed software vulnerabilities before patches are released. Rapid patching and upgrading limits susceptibility to zero-day attacks.
Third-Party Breaches
Third-party breaches target partners and vendors, exposing your data through interconnected systems and inadequate security. Vetting third parties and limiting access reduces this risk.
Essential Protective Measures
Repelling threats requires layered defenses tailored to your specific vessel including:
- Comprehensive security awareness training to identify and counter emerging social engineering, phishing, and other attack techniques.
- Strict access controls and least privilege roles to limit damage from compromised accounts and deter insider threats. Strictly limiting access and privileges based on user roles contains damage to only the compromised accounts and deters insider threats. Default to minimal access, only granting additional rights when essential.
- Add Multifactor authentication (MFA) across all sensitive systems and accounts to thwart stolen credentials. Requiring an additional login step beyond passwords blocks 99% of attacks.
- Secure file transfer methods and email security layers like DMARC and sandboxing to reduce malware risks.
- Automate and centralize patch management for swift and widespread software defect repair.
- Deploy Endpoint detection and response (EDR) solutions to monitor systems continuously and isolate threats even after breaches occur. Artificial intelligence spots and isolates threats missed by antivirus software.
- Complete data encryption to render sensitive information useless if stolen.
- Add Regular backups and emergency response plans for rapid recovery from ransomware and other attacks can get you back up and running quickly.
- Implement SIEM tools to help monitor IT infrastructure, detect anomalies, raise red flags, maintain logs, threat intelligence databases, compliance obligations, gaining & maintaining certifications, log management, and centralized security data.
- Employ 24/7 network monitoring, intrusion detection, and log analysis can help catch incoming attacks early.
- Schedule periodic cybersecurity audits and penetration testing to identify vulnerabilities proactively
- Carefully vetted cyber insurance to cover costs like legal damages and ransom payments
- Enlist Email Security and Sandboxing which helps deeply analyze attachments and links to detect stealthy threats. Sandboxing isolates and detonates suspicious files before delivery to block malware.
Ready to Outfit Your Ship?
The unfortunate reality is that a breach WILL occur. The threats are real and numerous but so are proven safeguards. It is a matter of when, not if. However, employing these methods and tools can help turn an iceberg into a hailstone.
With a strategic approach, watertight security is within reach. Let us assess your risks and craft a customized cybersecurity strategy tailored to your business. Contact us today to start fortifying defenses so you can set sail with confidence!